How to protect your computer from phishing attacks

Phishing attacks are a common and increasingly sophisticated method used by cybercriminals to steal personal information, such as passwords, credit card details, and other sensitive data. These attacks often involve emails or websites that appear to be legitimate but are designed to trick users into revealing their personal information. Here are some effective strategies to […]
How to encrypt your files
Protecting Your Data: A Guide to File Encryption In today’s digital world, data security is paramount. Whether it’s personal documents, financial information, or sensitive business data, protecting your files from unauthorized access is crucial. File encryption is a powerful tool that can safeguard your data, ensuring that only authorized individuals can access it. What is […]
Enhancing Your Security: A Guide to Implementing Multi-Factor Authentication
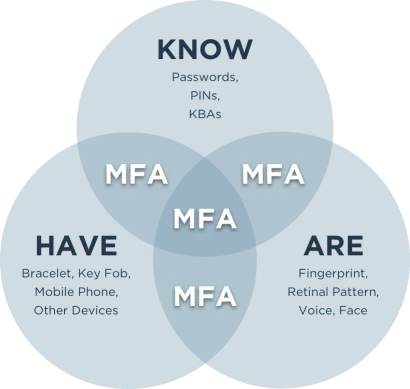
In today’s digital landscape, where cyber threats loom large, safeguarding our online presence has become more critical than ever. With the increasing sophistication of hacking techniques, relying solely on passwords for security is no longer sufficient. This is where multi-factor authentication (MFA) emerges as a powerful shield, providing an additional layer of protection to your […]
How to troubleshoot network connectivity issues

Troubleshooting network connectivity issues can be a complex task, but a systematic approach can help you identify and resolve the problem. Here’s a general guide for troubleshooting network connectivity issues: Identify the scope of the issue: Determine whether the problem is affecting a single device or multiple devices on the network. This helps narrow down […]
How to configure a firewall

Configuring a firewall involves several steps to ensure the security of your network. The specific steps may vary depending on the type of firewall and its interface, but the general process typically involves: Secure the firewall itself: Update the firewall’s firmware to the latest version to address any known vulnerabilities. Change default passwords and disable […]
How to set up a VPN

Setting up a VPN can be a straightforward process, and the specific steps may vary slightly depending on the VPN provider and the device you’re using. However, the general process involves the following steps: Choose a VPN provider: There are numerous VPN providers available, each offering different features, pricing plans, and server locations. Research and […]
How to customize your Windows desktop
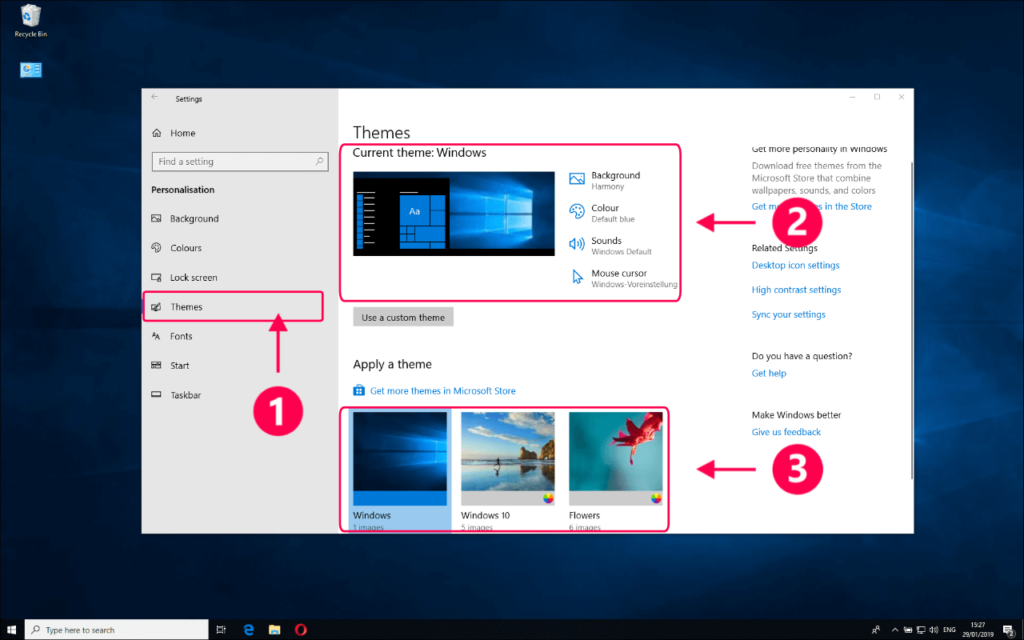
Customizing your Windows desktop is a great way to personalize your computing experience and create a workspace that reflects your style and preferences. Here’s a step-by-step guide to customizing your Windows desktop: Personalize Your Background: Right-click on an empty area of your desktop and select “Personalize”. This will open the Personalization settings where you can […]
How to manage your Windows user accounts
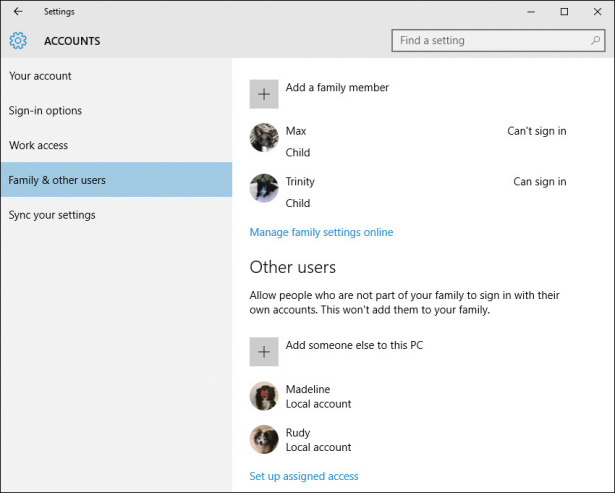
Managing user accounts in Windows is crucial for maintaining security, privacy, and control over your system. Whether you’re a home user or a system administrator, understanding the basics of user account management is essential. Creating and Modifying User Accounts: Accessing User Account Settings: To access user account settings, open the “Settings” app and navigate to […]
Unlocking the Power of Automation: A Beginner’s Guide to Windows PowerShell

In the realm of system administration and automation, Windows PowerShell stands as a versatile and powerful tool, capable of streamlining tasks and enhancing control over your Windows environment. Whether you’re a seasoned IT professional or a curious newcomer, delving into the world of PowerShell can open doors to enhanced efficiency and a deeper understanding of […]
